The MySejahtera app has been revealed to have security vulnerabilities that allow anyone to send out emails or one-time passwords (OTP) on behalf of the app, leading to concerns over personal data breaches.
The MySejahtera team has since said they have blocked the exploit that made it possible to send out OTPs on behalf of the app and is in the midst of enhancing the app’s security. They have yet to address the email exploit.
The matter was first brought to Malaysiakini’s attention by full-stack developer Phakorn Kiong, who had initially highlighted the issue in several postings online.
“In usual design, there are supposed to be ‘keys’ where the server can use to identify who is calling the server (as a form of authentication).
“The problem with this design is there are no ‘locks’ implemented. Anyone can come in and abuse the APIs (application programming interface).
“With this exploit, I can send emails on behalf of MySejahtera, as you may have received,” Kiong said to Malaysiakini.
APIs are software intermediaries that allow two applications to talk to each other.
Possible to extract personal information
Kiong had also earlier sent an email on behalf of MySejahtera to Malaysiakini to prove the vulnerabilities existed.
He said this exploit could potentially be used by “bad-faith actors” to send out emails with bad intentions from an official-sounding source.
This is because the content of the email can be altered through the exploit and in some cases, files can also be attached to the email.
Meanwhile, the OTP issue was first brought up on the popular lowyat.net forum.
Kiong said it is also possible for people to extract phone numbers and emails registered with the MySejahtera Check-In feature through the security exploit.
“Imagine the amount of exposure. Most premises in Malaysia now need to register for the MySejahtera Check-In to create the QR code,” he said.
The MySejahtera team said last night that they have been receiving complaints about people receiving unsolicited OTP messages to verify their phone number for the check-in QR registration.
The team said their investigation found that the check-in QR registration feature, which was meant for business premises, has been misused by “malicious scripts” to send OTP to random phone numbers.
“Since then, these API endpoints are blocked and a fix to enhance security will be moved tonight.
“We want to reassure all our users that no user data was accessed by these scripts but random phone numbers were spammed to verify their phone number. We apologise for this inconvenience,” the MySejahtera team said in a statement last night.
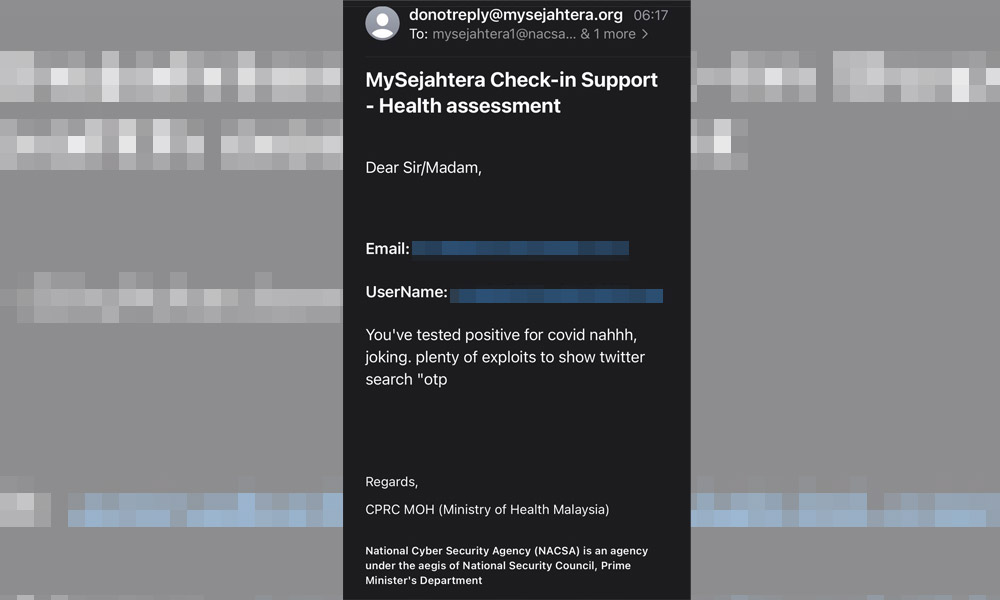
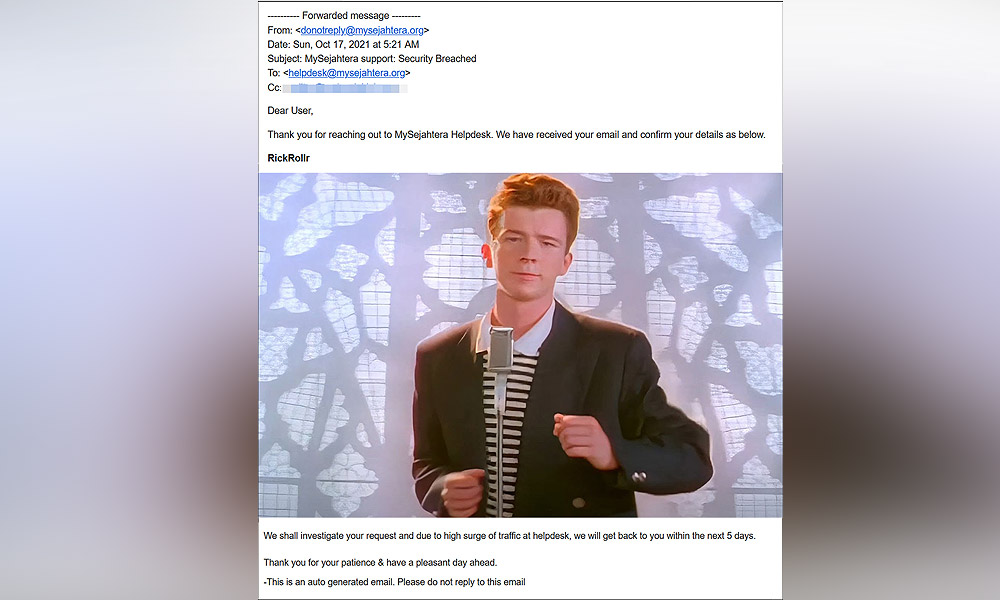
While they appear to have addressed the OTP issue, a number of people reported receiving fake emails from the MySejahtera email address this morning.
Some were told they had been confirmed positive for Covid-19 followed by an acknowledgement that this was a joke and was sent out due to an exploit in the system.
Others received emails from the MySejahtera email address that included a popular meme involving British singer Rick Astley and his song ‘Never Gonna Give You Up’.
The MySejahtera team has said it will issue an updated statement on this matter later today.
'Door wide open'
Kiong told Malaysiakini today that the issue has been partly addressed by the MySejahtera team as they have added a reCAPTCHA system to prevent scripts and bots from abusing the app.
However, Kiong said this is not an effective solution as there are cheap services that can bypass the reCAPTCHA system and it also does not stop humans from exploiting the security vulnerabilities.
“I want them to fix it once and for all. I can still send out fake emails with the reCAPTCHA system in place.
“They (MySejahtera) are supposed to implement more checks. It is like a door that is wide open and they have just closed the door a little bit. There isn’t even a padlock,” he said.
Those who are interested in a more detailed and technical explanation of the security vulnerabilities can find Kiong’s postings on the matter here and here. - Mkini



No comments:
Post a Comment
Note: Only a member of this blog may post a comment.